Primary Sanctions
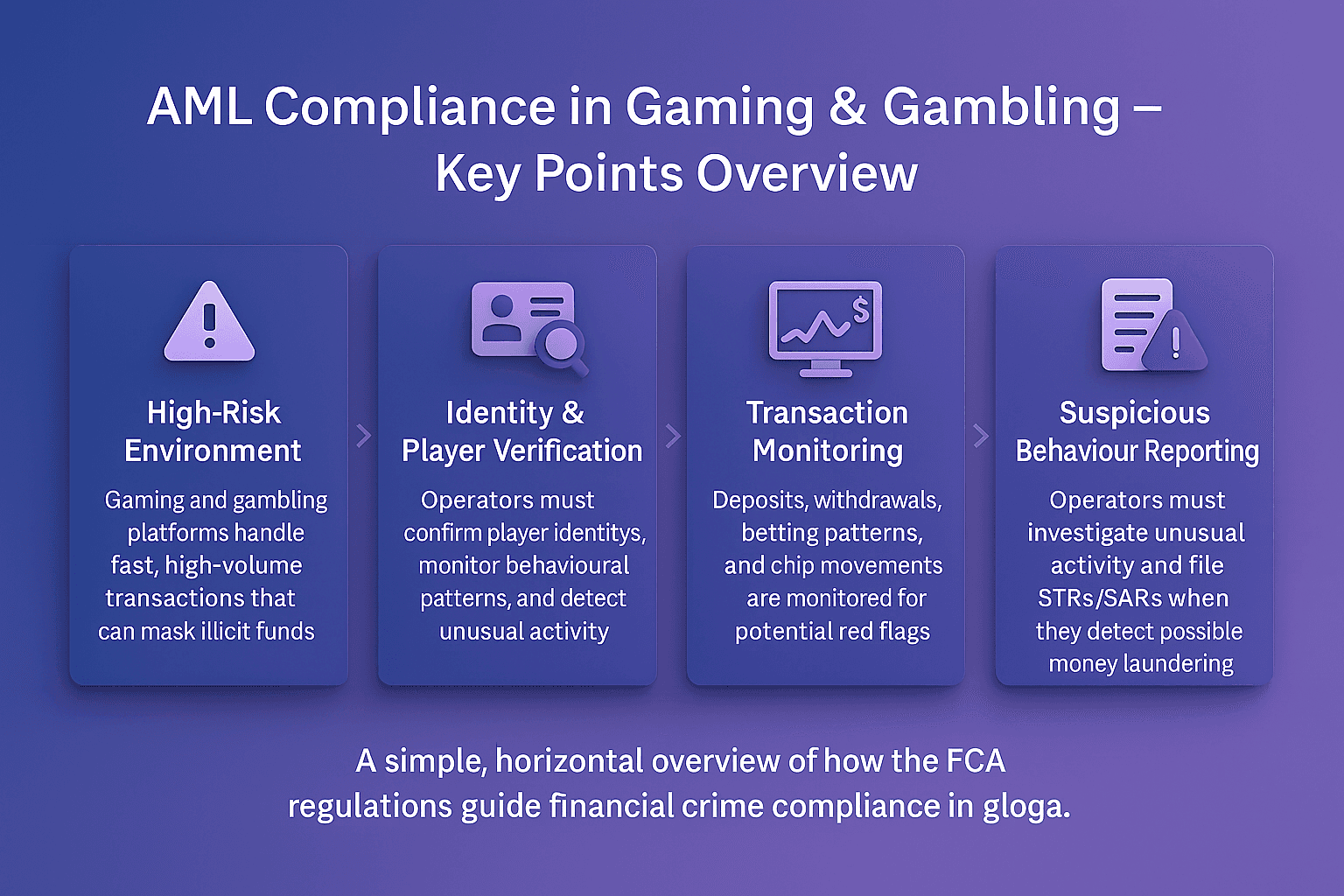
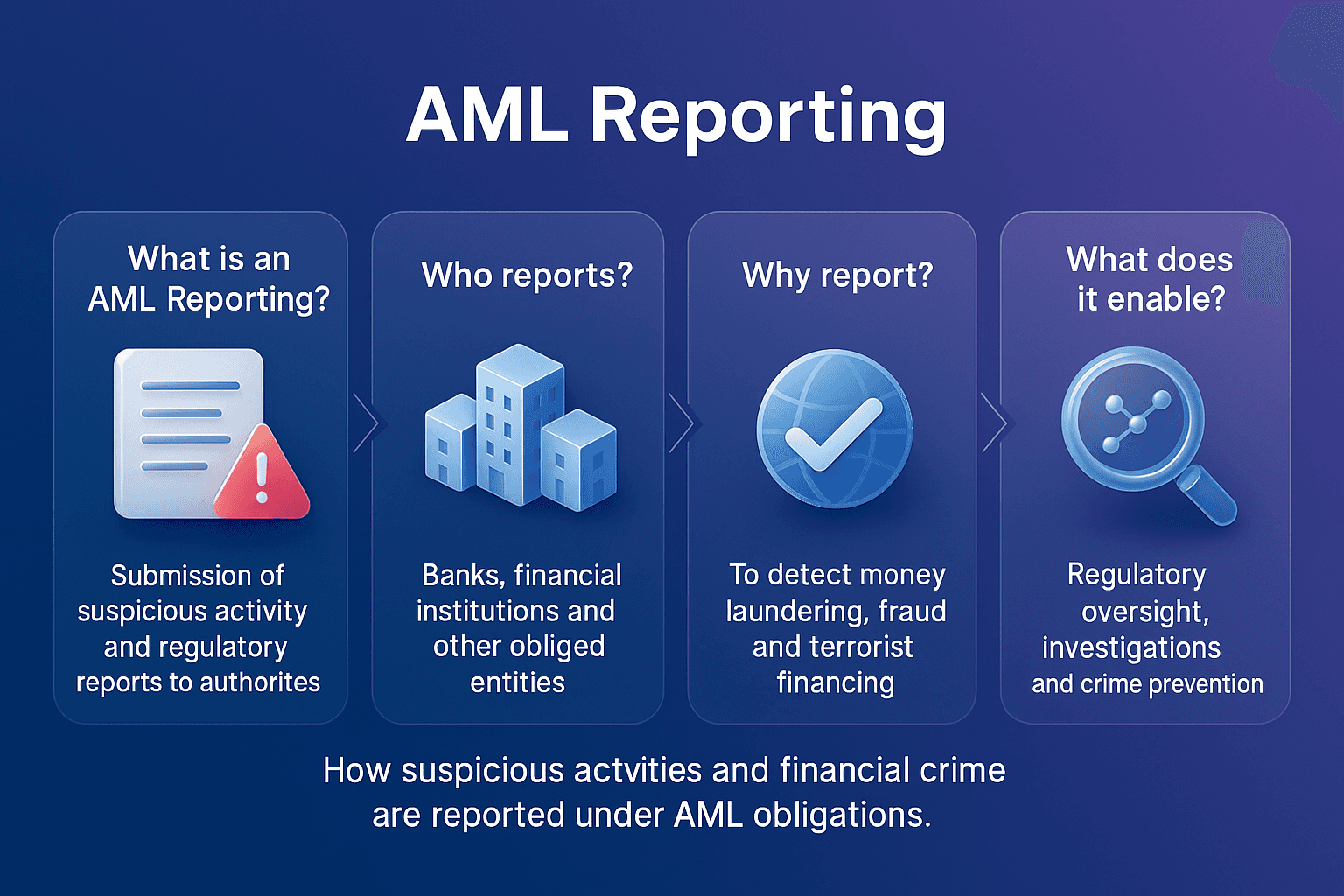
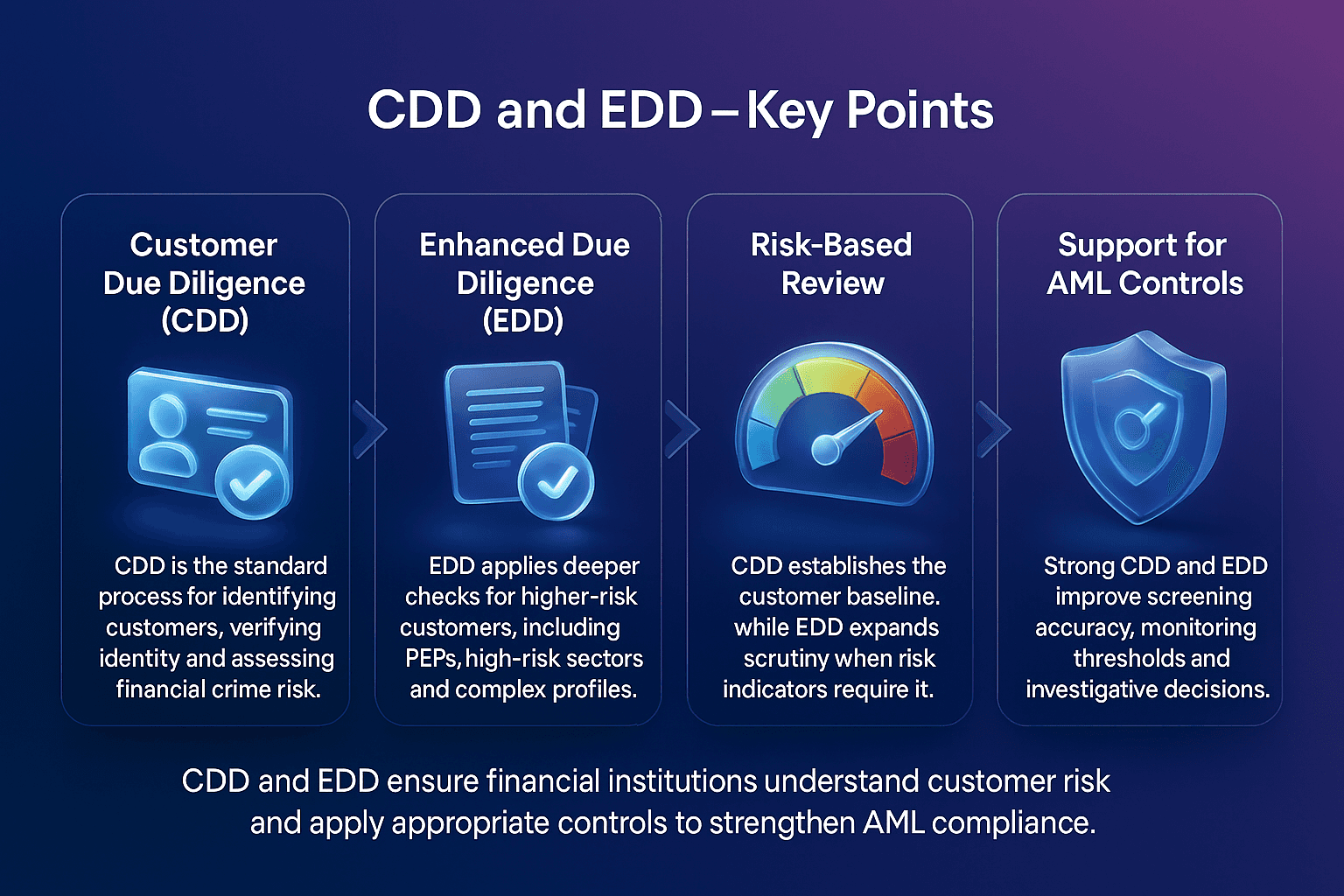
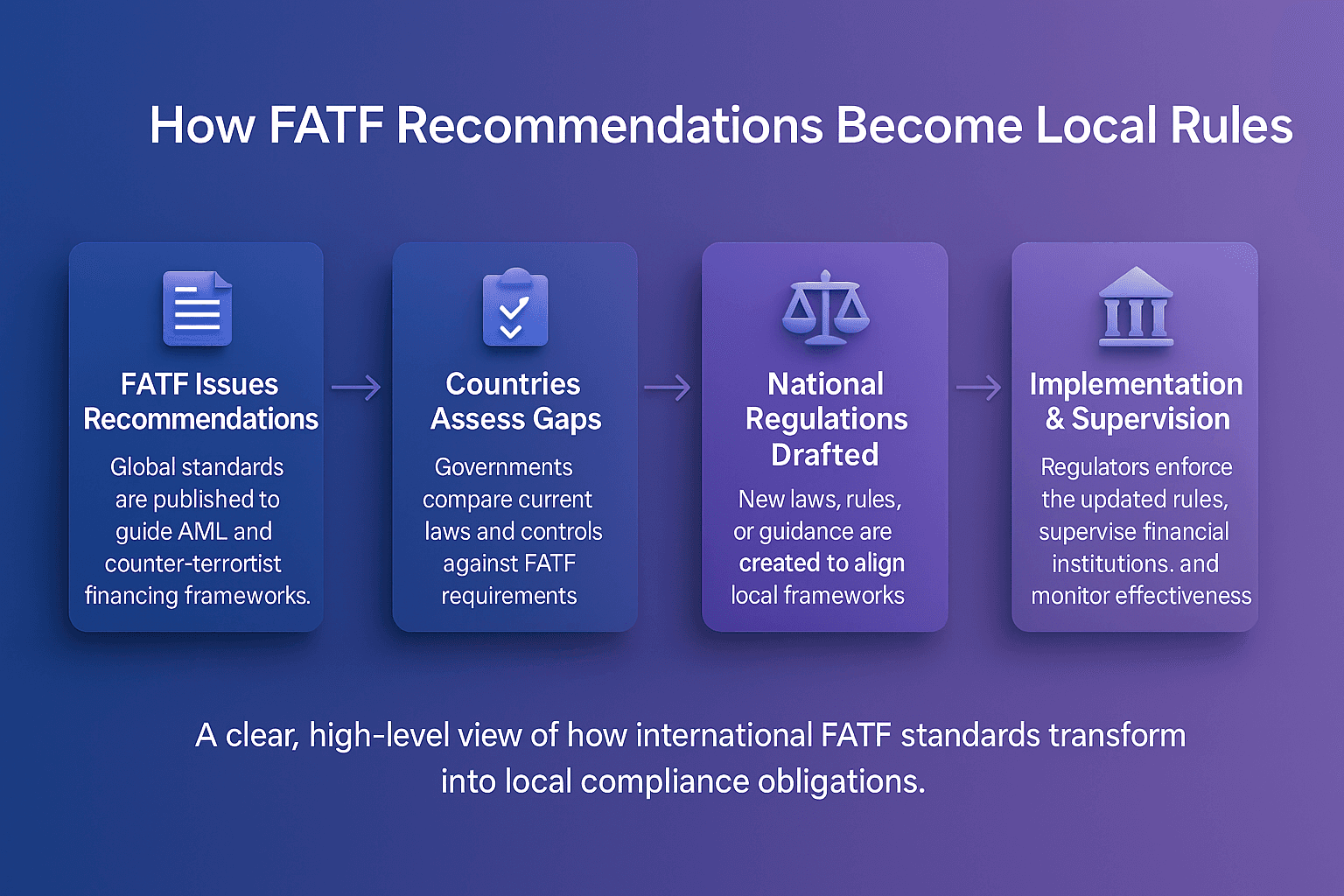
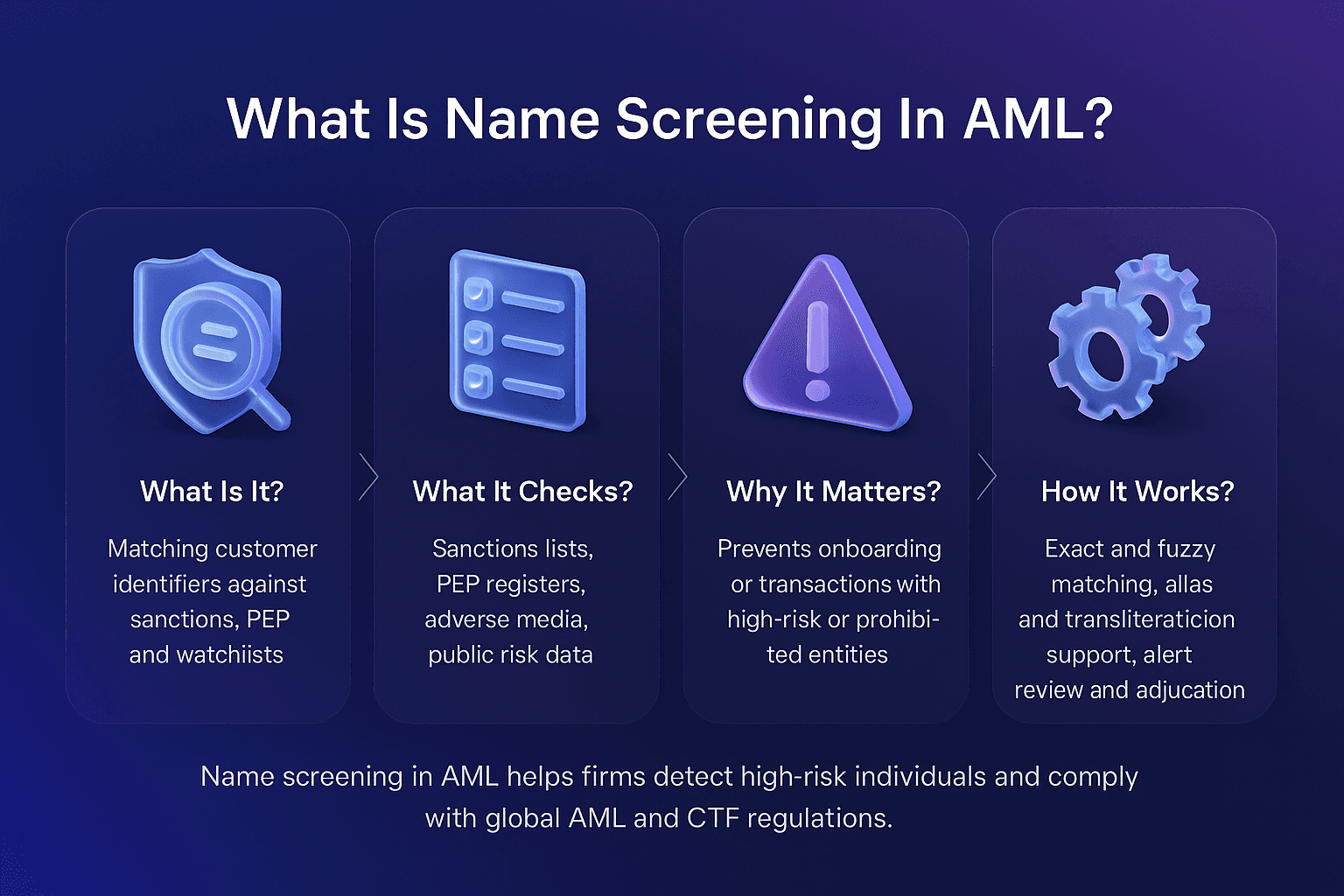
Primary sanctions are restrictions imposed by a government or regulatory authority that prohibit its own citizens, companies, and financial institutions from engaging in specified types of financial activity with sanctioned individuals, entities, or jurisdictions.
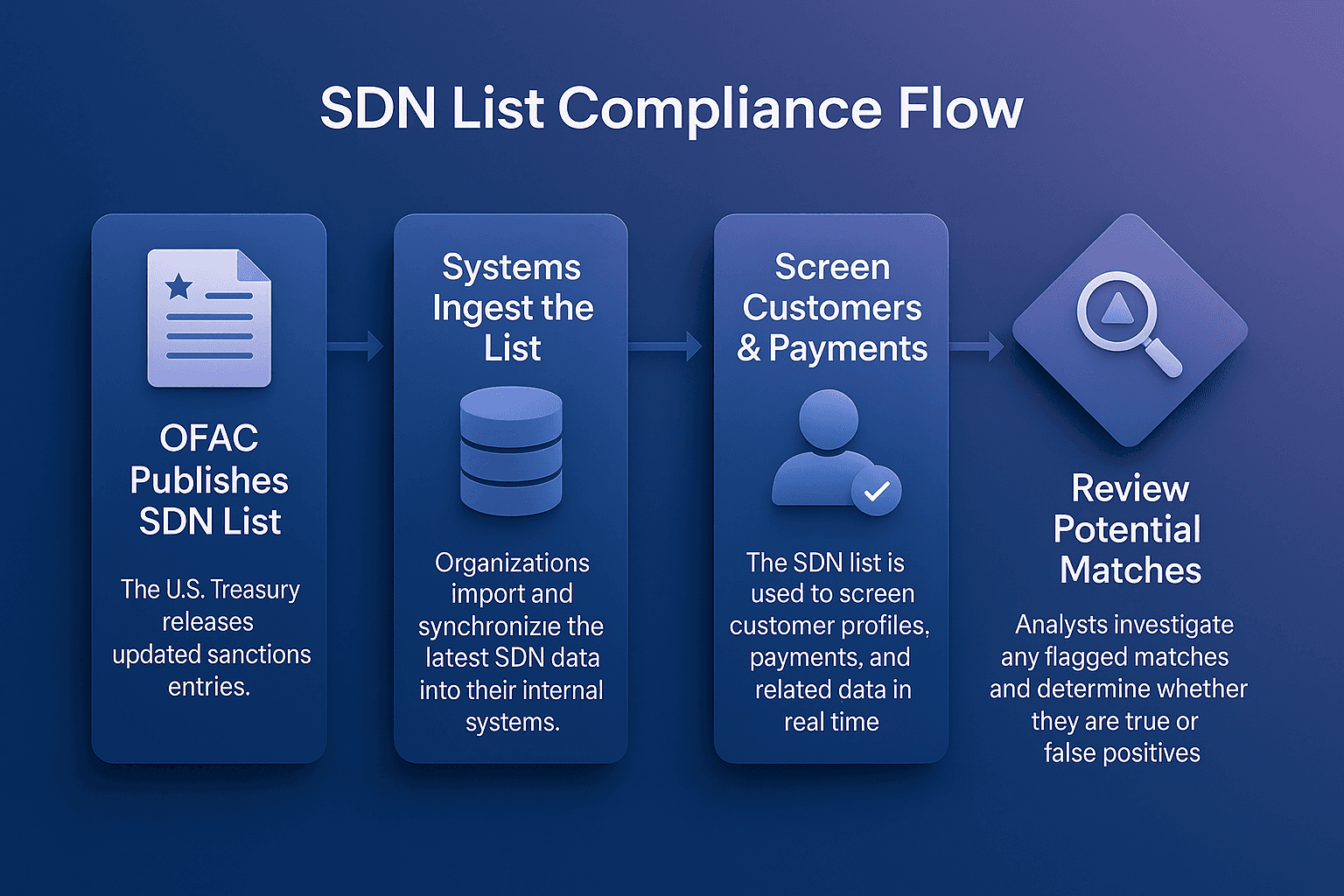
For example, U.S. primary sanctions administered by the Office of Foreign Assets Control (OFAC) prohibit U.S. persons and companies from conducting business with individuals or organizations listed on the Specially Designated Nationals (SDN) list.
In AML compliance, understanding and adhering to primary sanctions is essential for preventing violations, avoiding penalties, and maintaining trust with regulators.
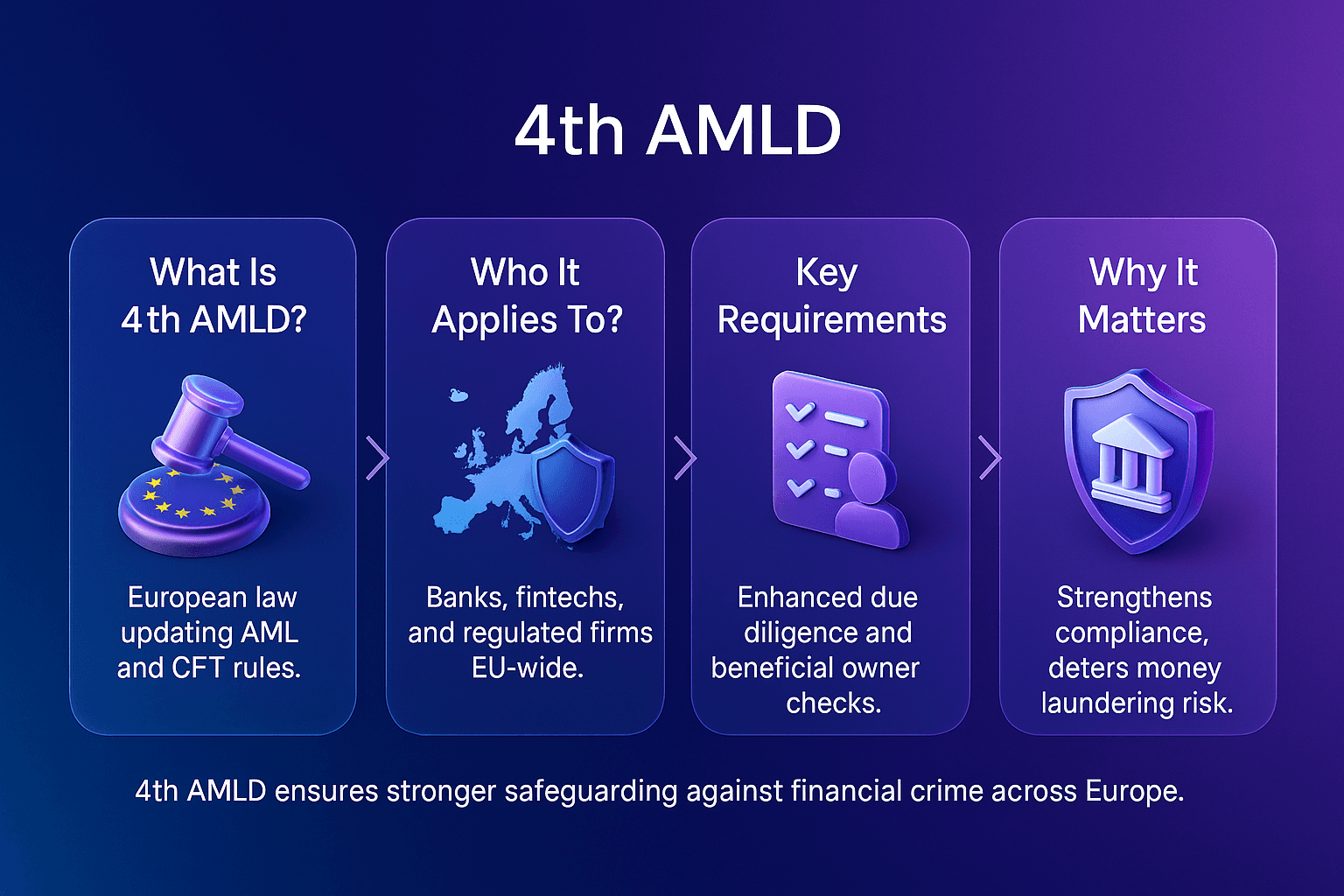
Primary Sanctions
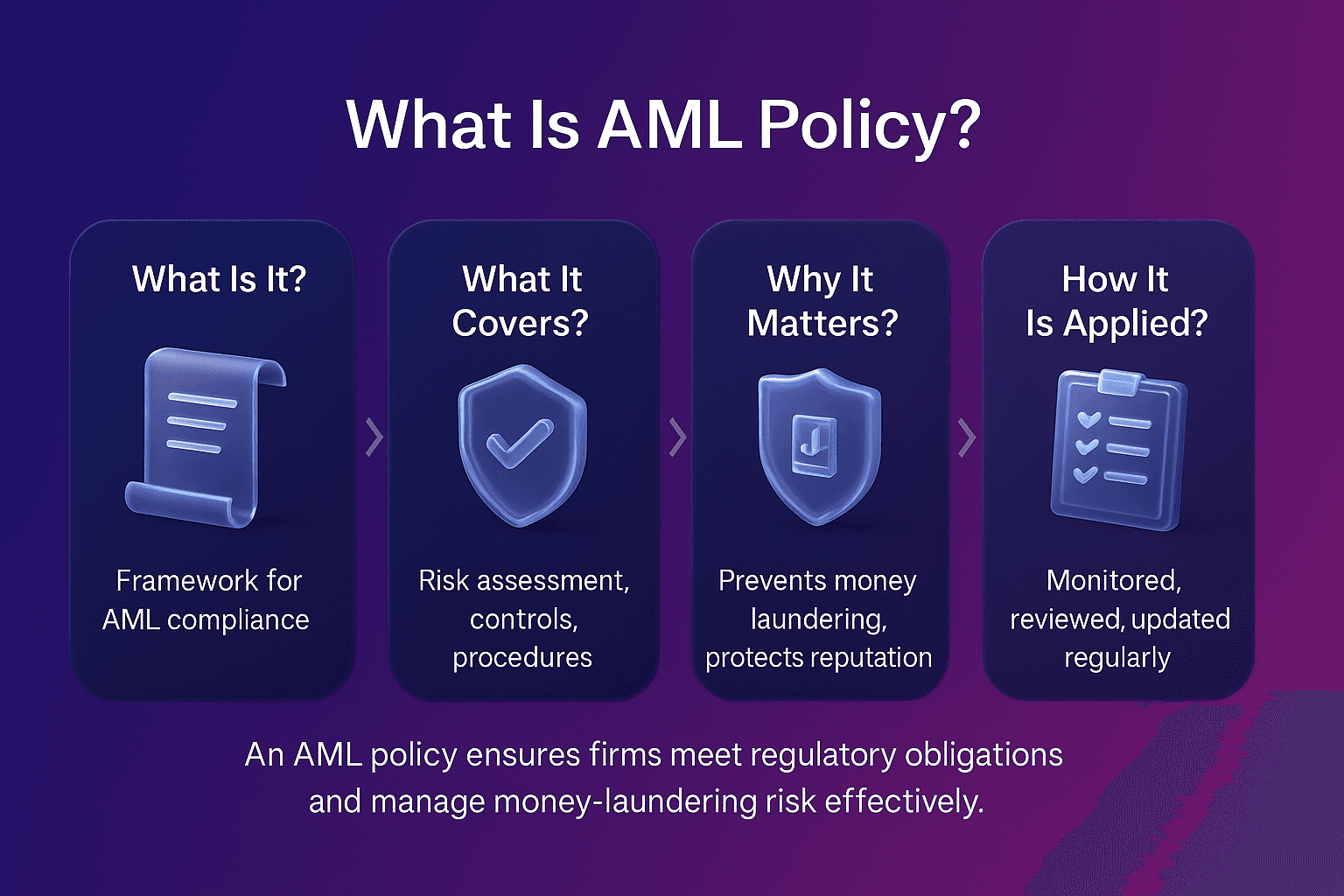
Primary sanctions are legal obligations that bind domestic persons and institutions, requiring them to block or restrict transactions with designated entities. Unlike secondary sanctions, which target non-domestic actors, primary sanctions focus on the direct obligations of individuals and businesses under the jurisdiction of the sanctioning authority.
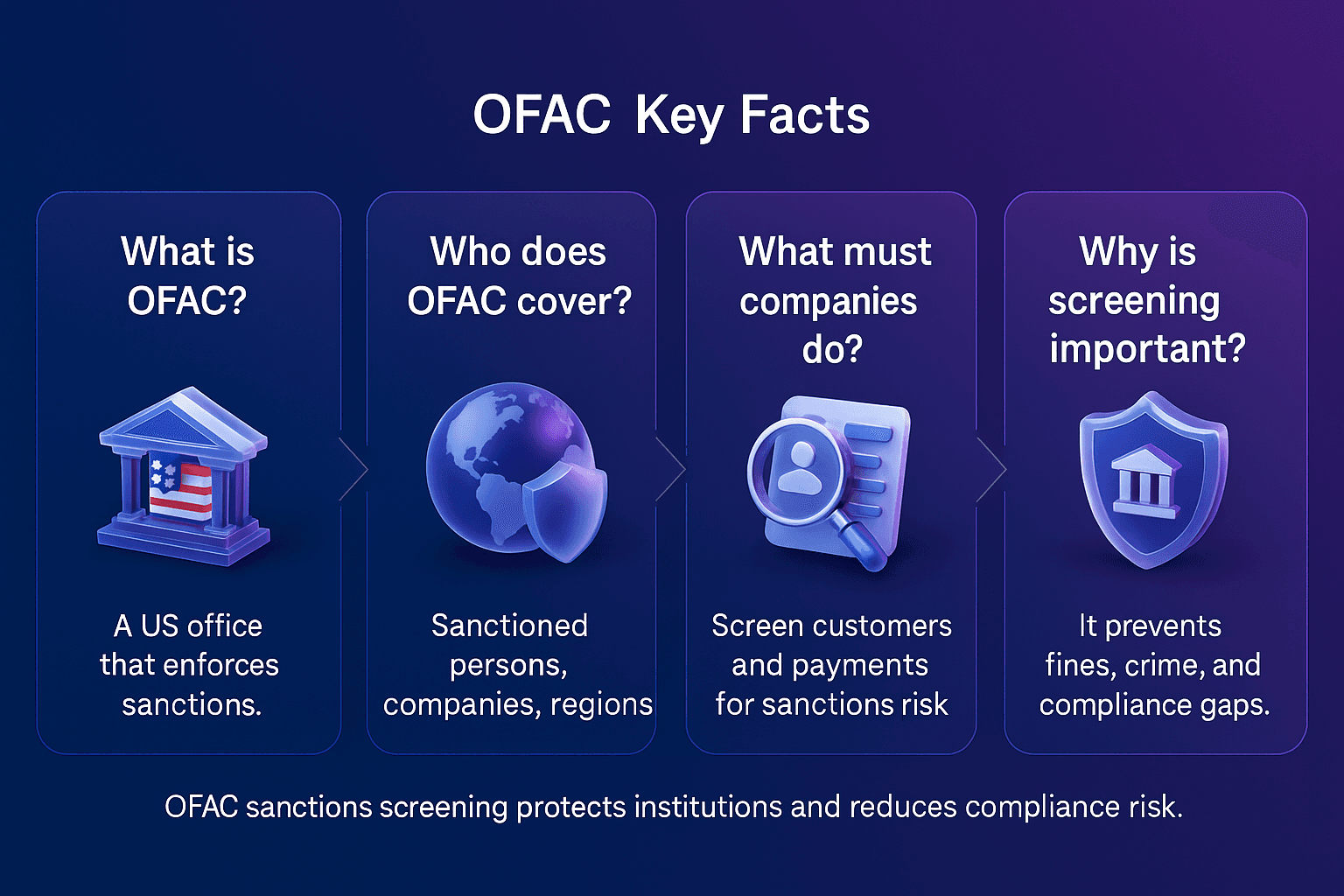
The U.S. Department of the Treasury outlines how primary sanctions prohibit U.S. persons from engaging in transactions with blocked entities, ensuring that sanctioned actors are excluded from the U.S. financial system, as detailed in the OFAC “Basic Information on OFAC and Sanctions” FAQ
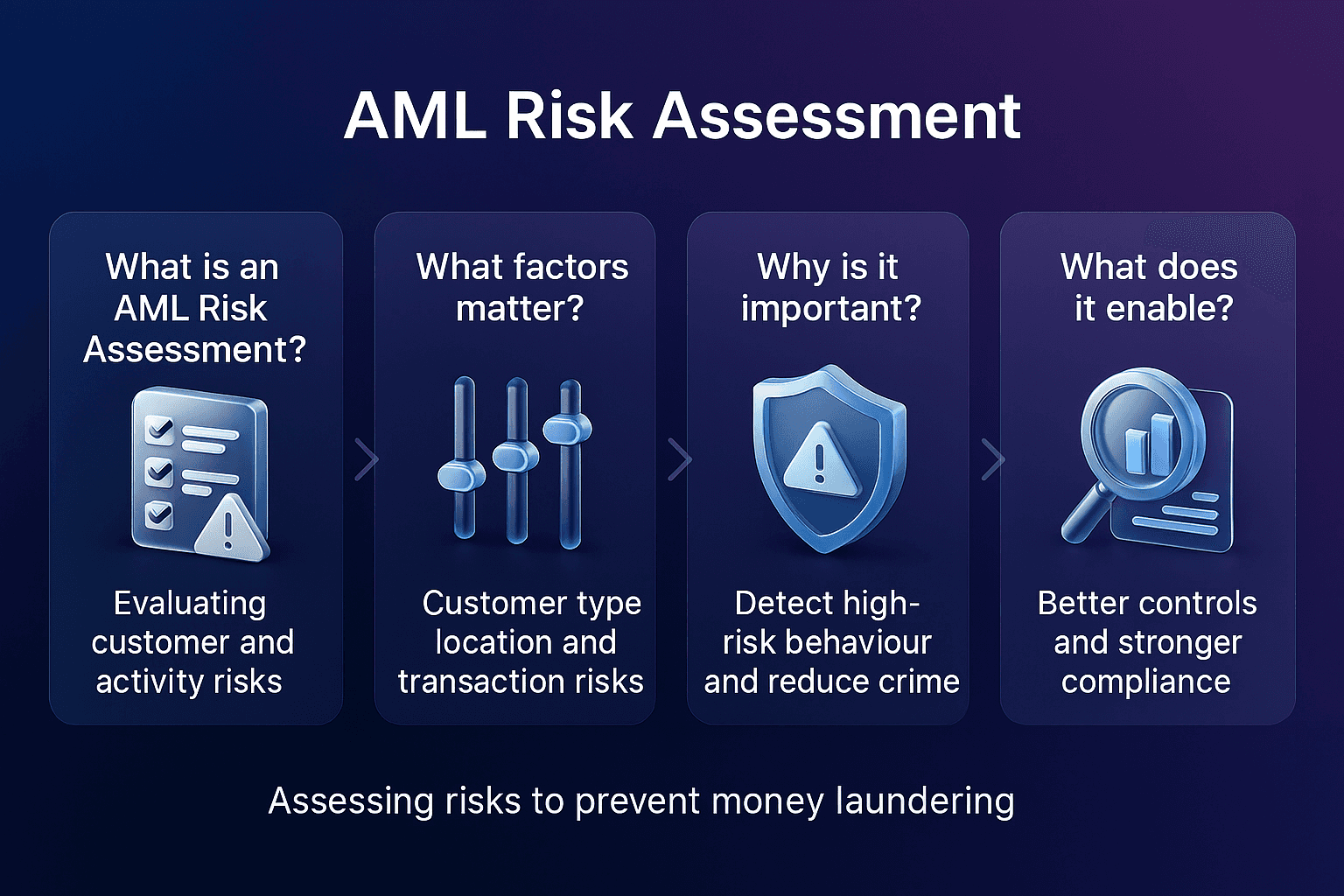
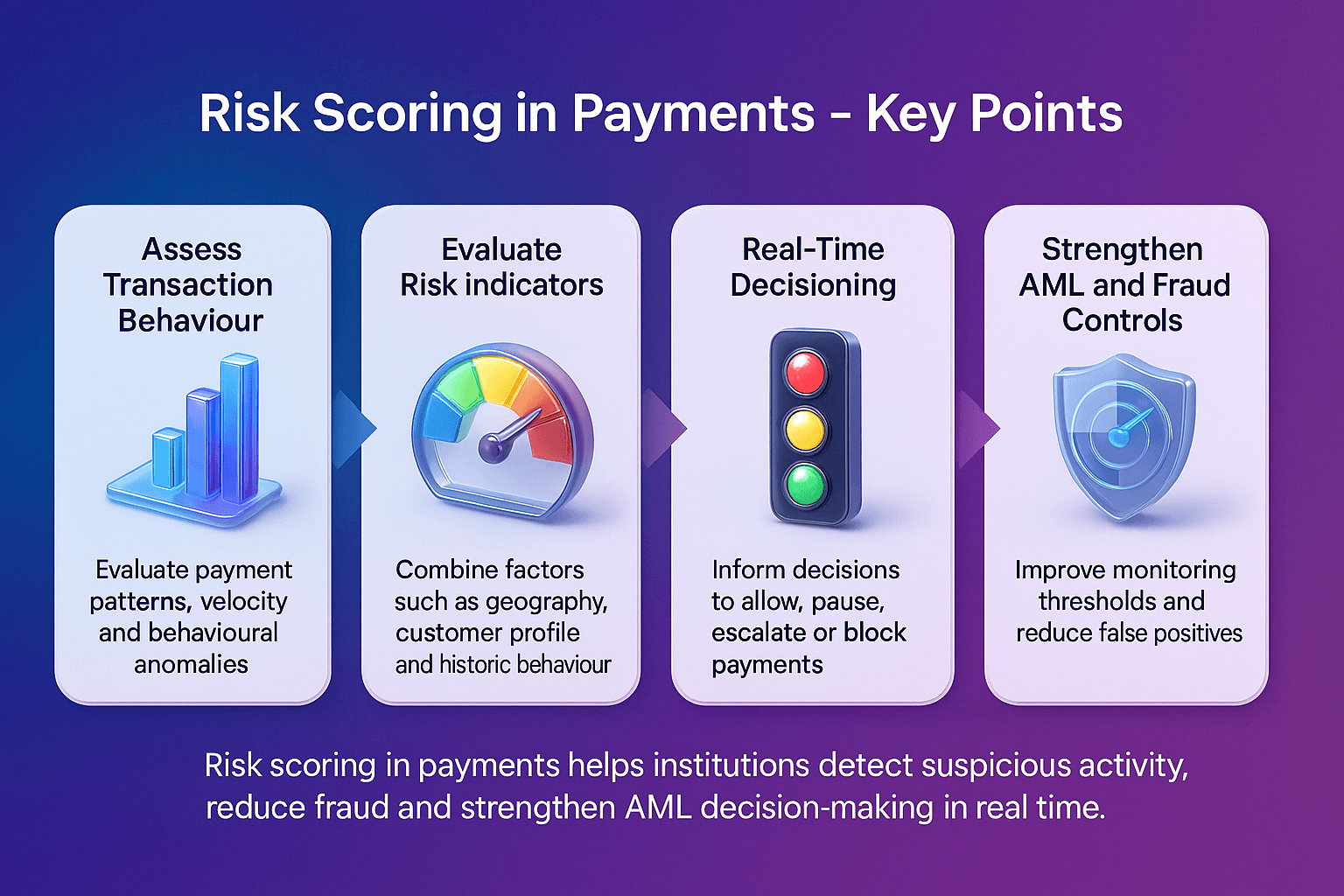
Why Primary Sanctions Matter In AML Compliance
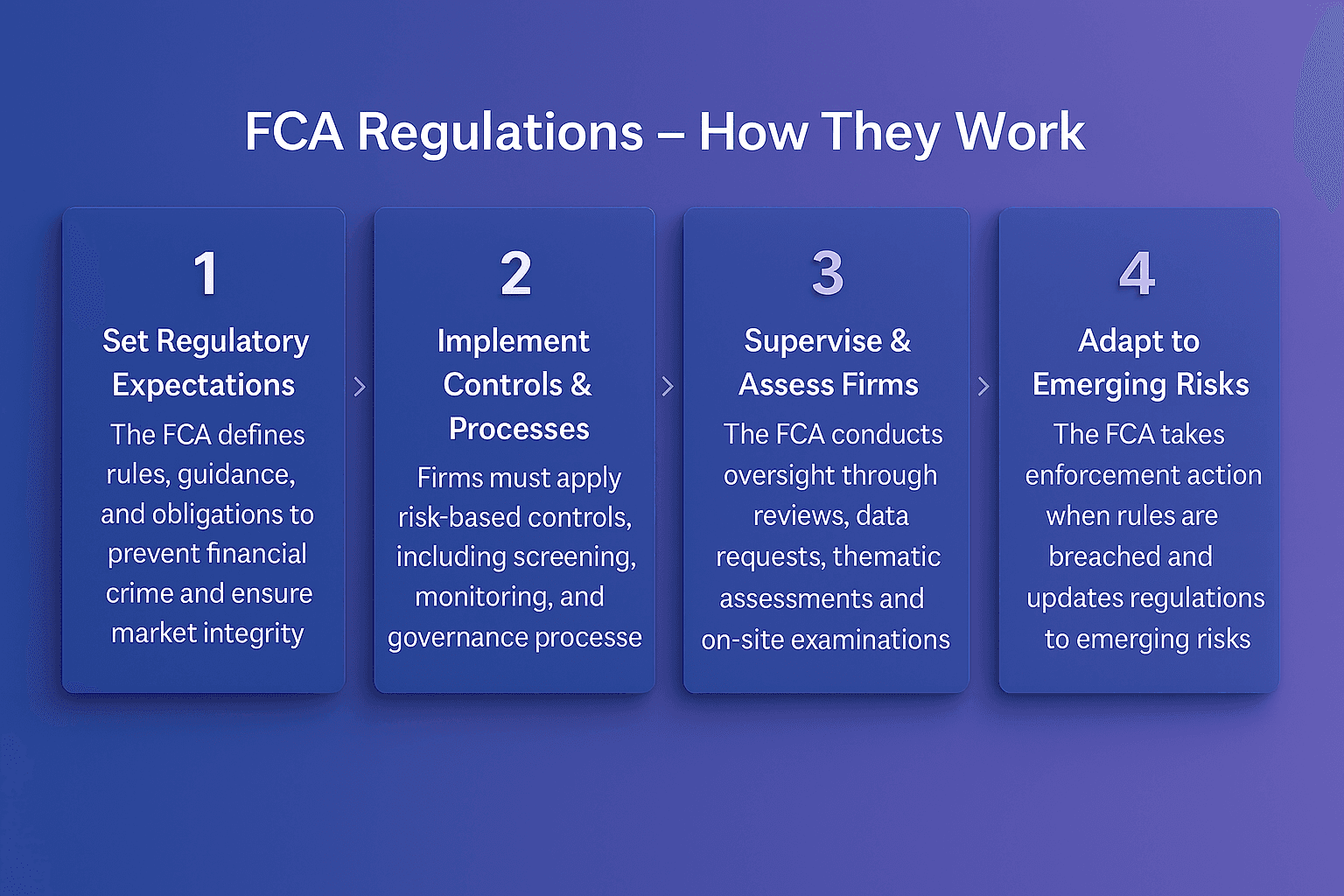
Primary sanctions are critical because they directly influence how financial institutions design their compliance frameworks. According to OFAC’s official announcement, firms must have robust systems in place to prevent transactions with sanctioned entities.
Key reasons primary sanctions matter include:
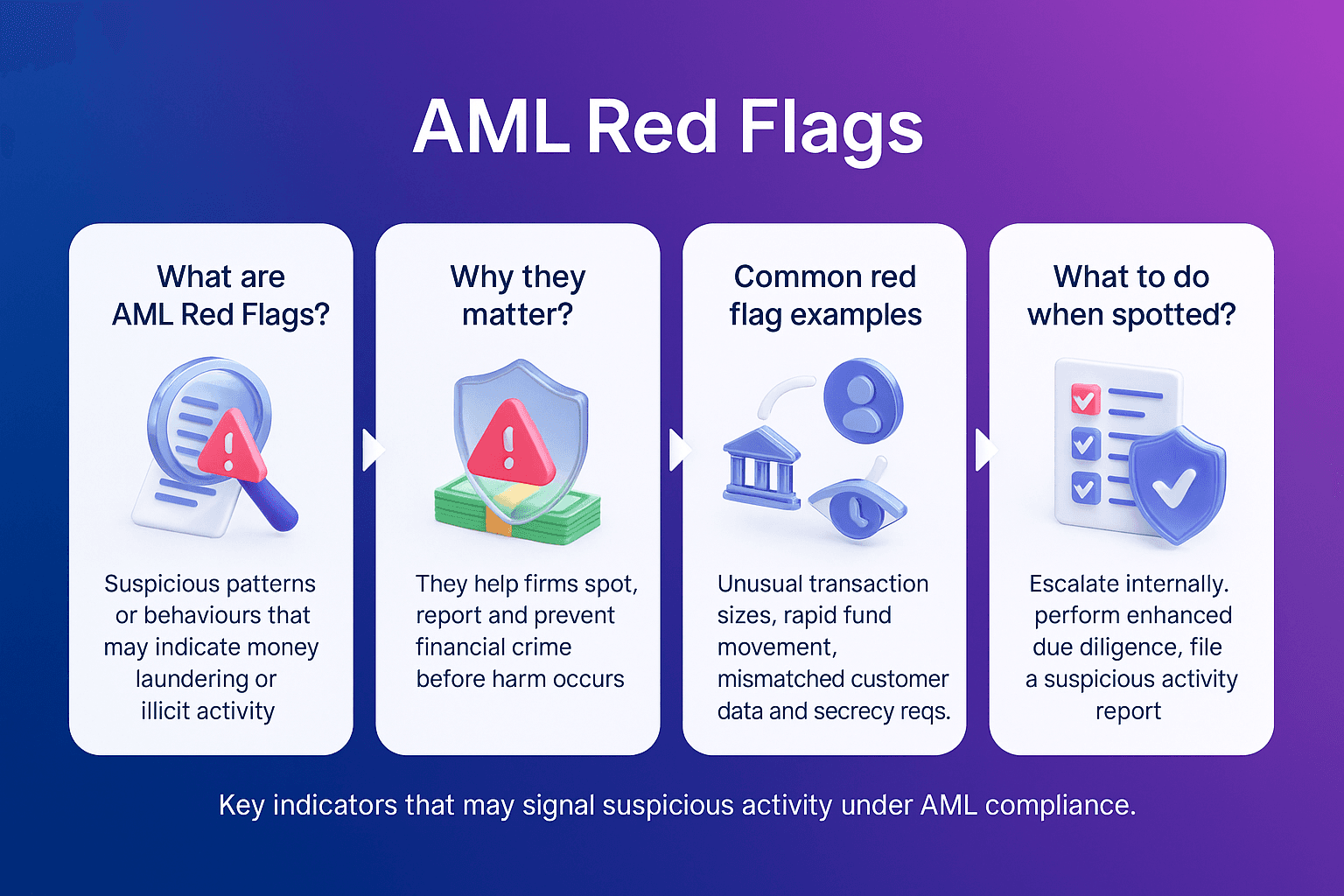
Legal obligation: Breaching primary sanctions can lead to heavy fines and reputational damage
Operational impact: Institutions must screen all customers and transactions against sanctions lists
Risk-based compliance: Sanctions enforcement emphasizes risk awareness across all business lines
Global influence: Even non-sanctioning countries often align with primary sanctions to maintain financial system access
Examples Of Primary Sanctions
Primary sanctions vary by jurisdiction but often include:
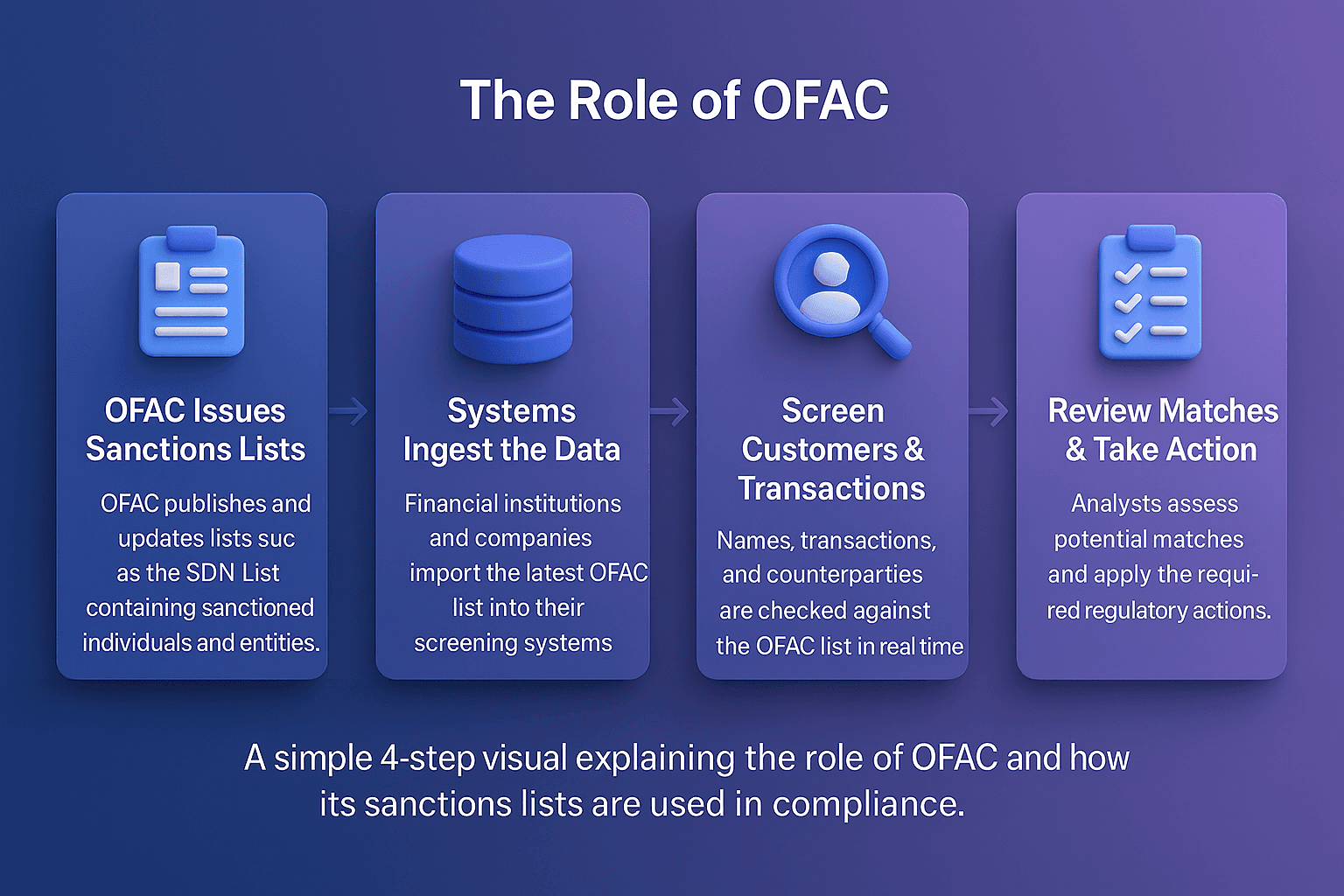
U.S. Sanctions: Restrictions by OFAC, such as prohibitions against dealing with entities on the SDN list
EU Sanctions: Measures adopted by the European Union Council restricting EU persons from specific transactions
UK Sanctions: Rules enforced under the UK Sanctions and Anti-Money Laundering Act 2018 requiring UK firms to block dealings with designated persons
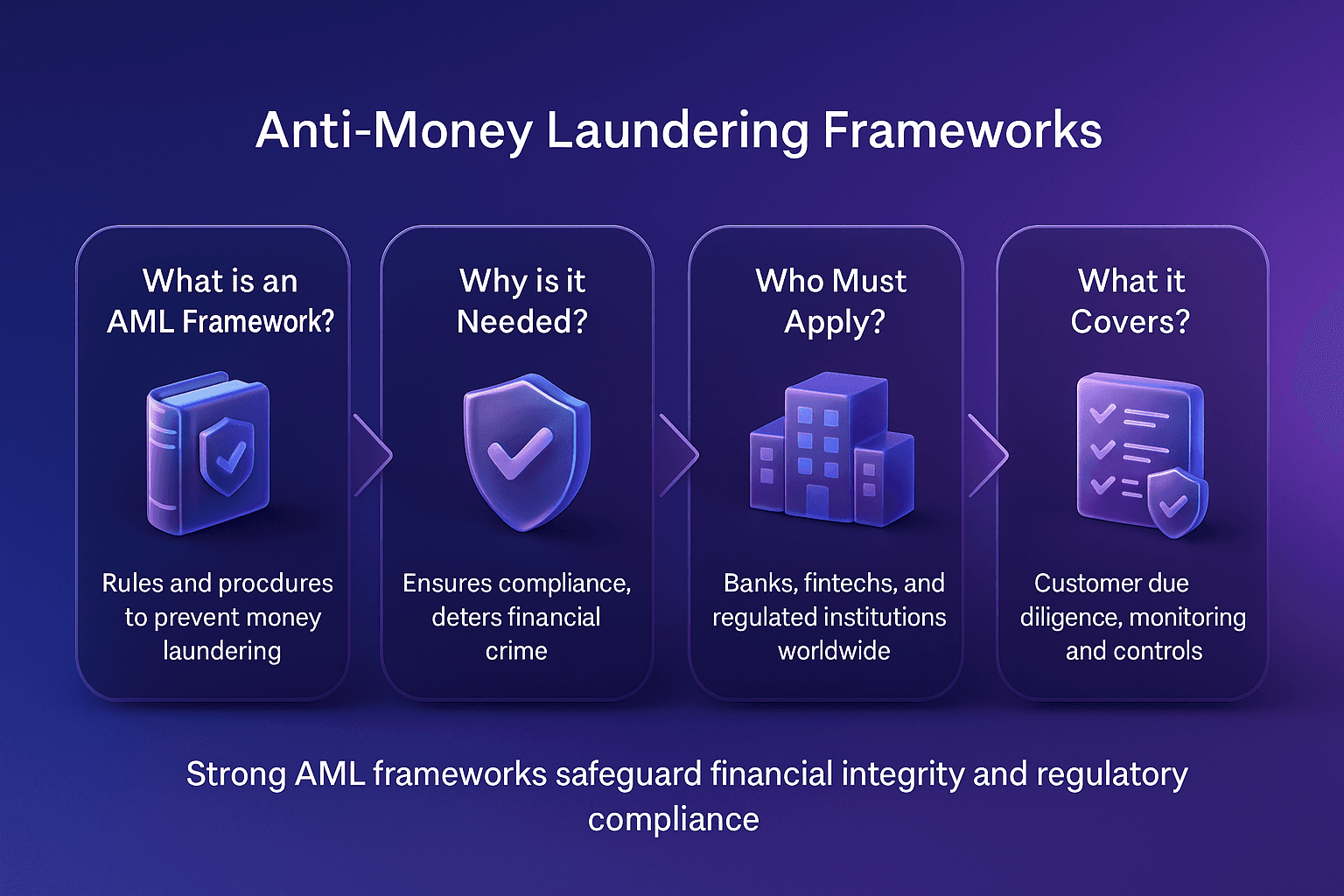
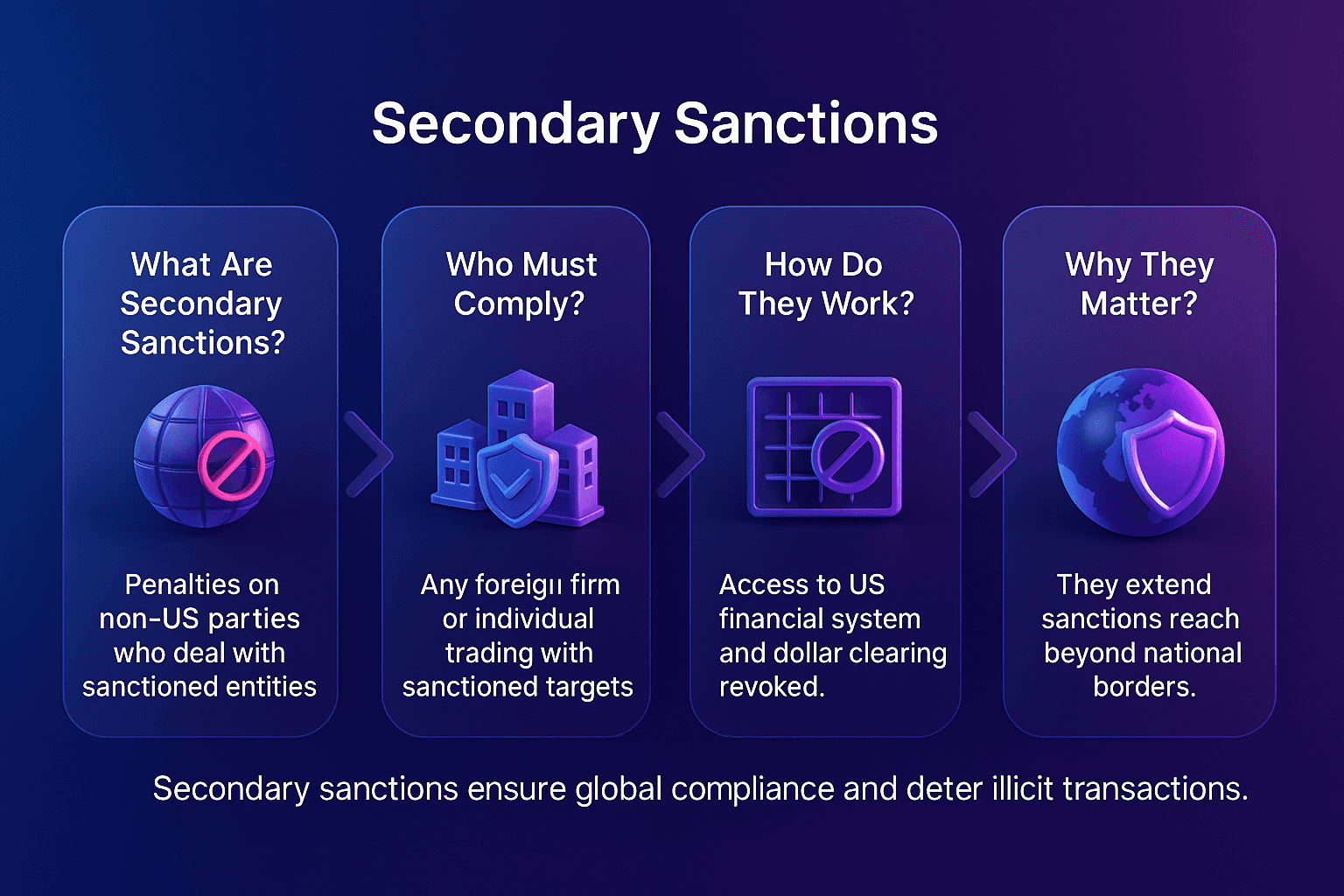
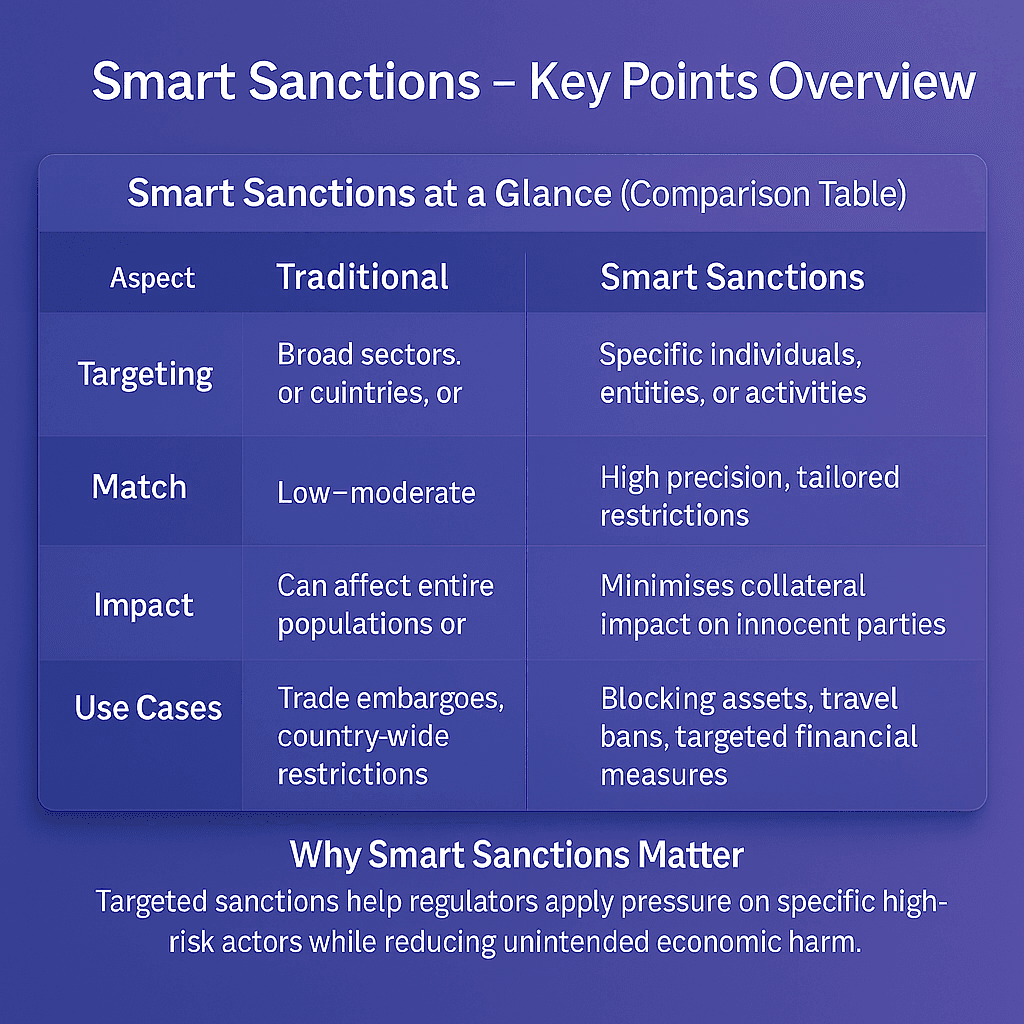
Primary Sanctions vs Secondary Sanctions
It’s important to distinguish primary sanctions from secondary sanctions:
Primary sanctions apply to persons and entities under the sanctioning country’s jurisdiction (e.g., U.S. citizens, U.S.-based companies).
Secondary sanctions extend beyond borders, penalizing foreign persons or entities that do business with sanctioned parties.
Together, these measures form a powerful enforcement mechanism in the global AML framework.
The Future Of Primary Sanctions
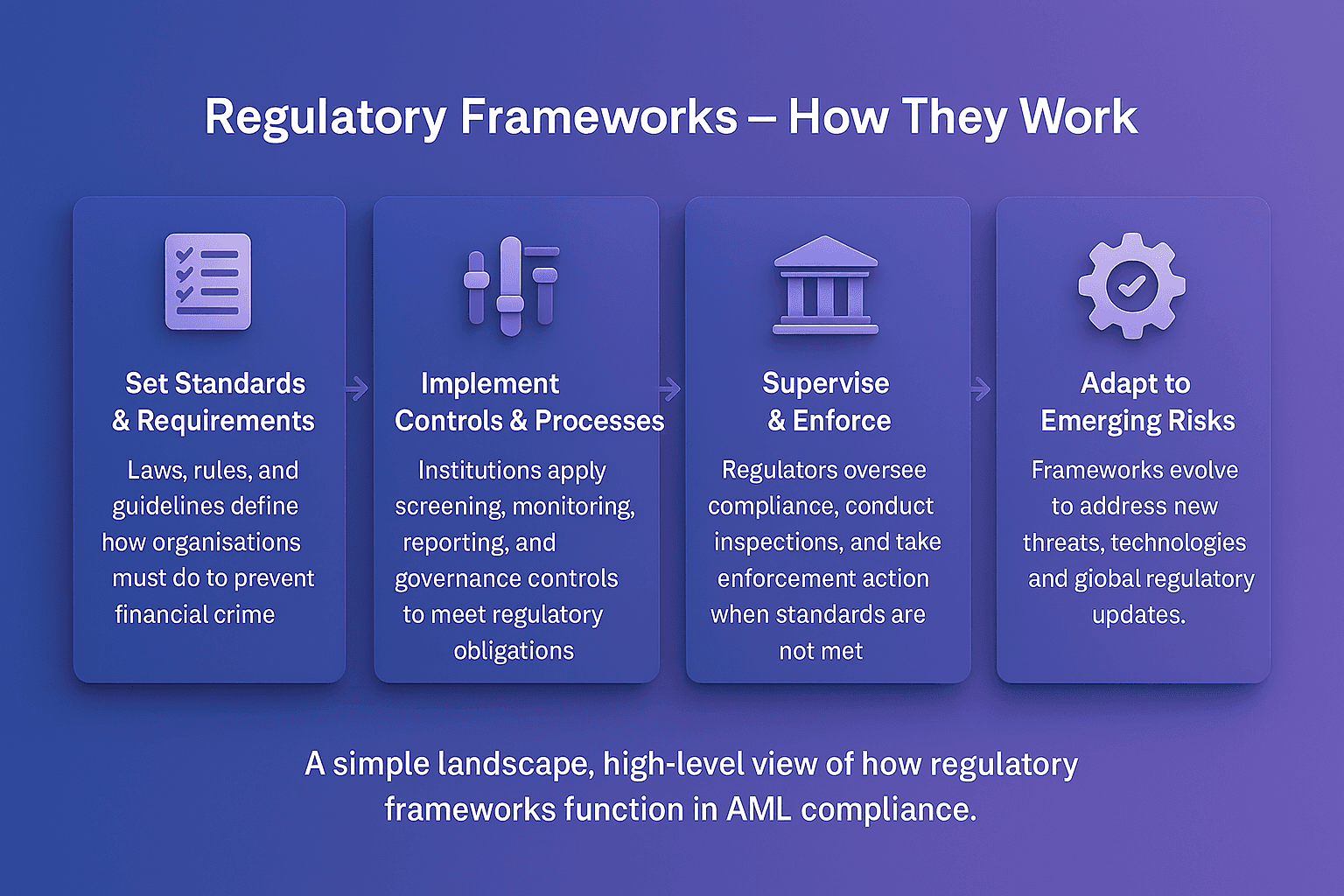
The future of primary sanctions will be shaped by growing geopolitical complexity and advances in compliance technology.
Trends include:
Broader scope of sanctions to include cyber-related crimes and digital assets
Integration of real-time monitoring tools to ensure instant compliance with sanctions lists
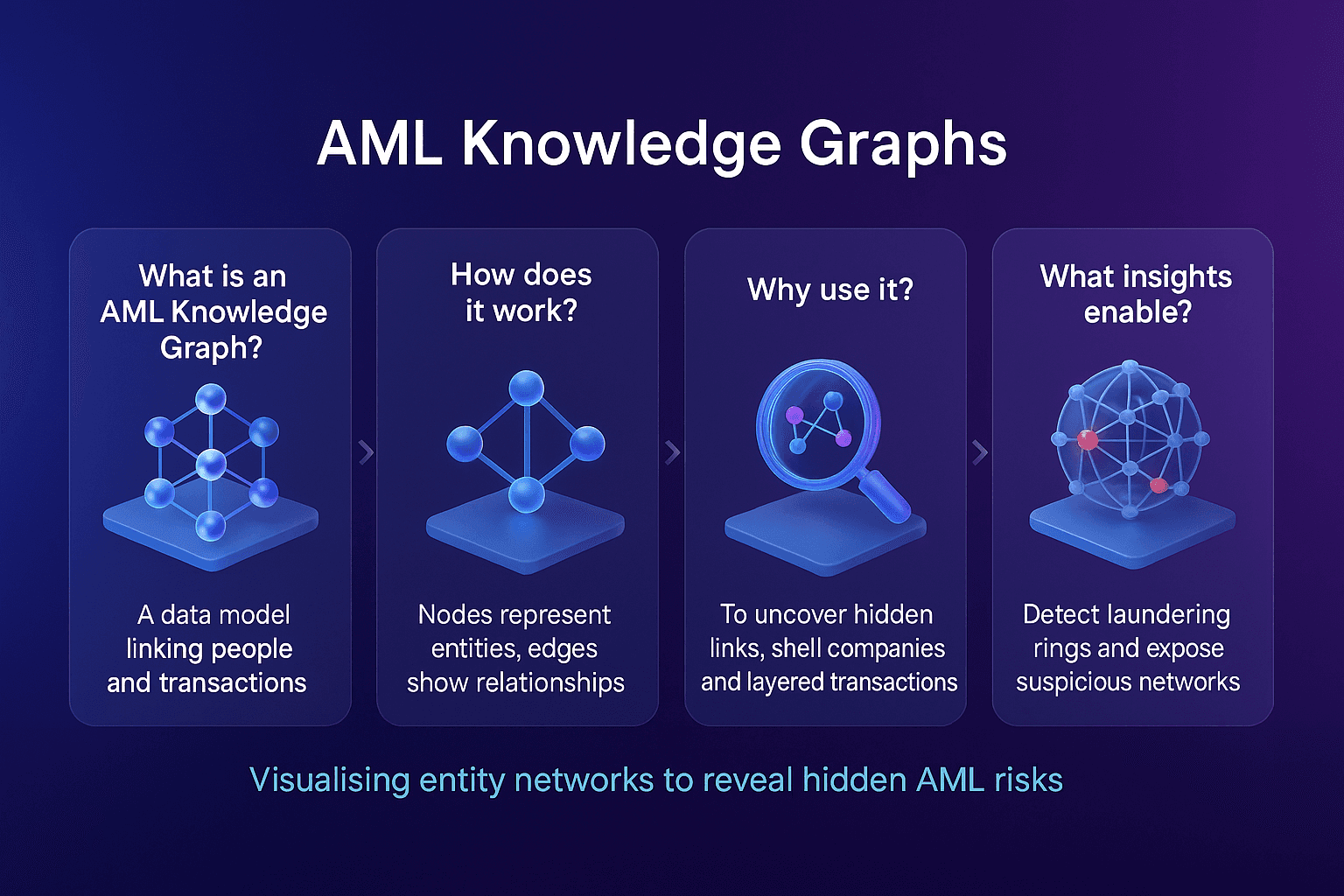
Use of AI and graph analytics to detect hidden networks behind sanctioned entities
Greater alignment of sanctions regimes across the U.S., UK, and EU for coordinated enforcement
Institutions will increasingly need to modernize systems to keep pace with evolving sanctions regimes and regulatory expectations.
Strengthen Your AML Framework With Effective Sanctions Compliance
Adhering to primary sanctions is non-negotiable. By implementing robust screening, monitoring, and adjudication systems, institutions can reduce risk, avoid costly penalties, and ensure regulatory compliance.
👉 Contact Us Today To Strengthen Your AML Compliance Framework
Learn more
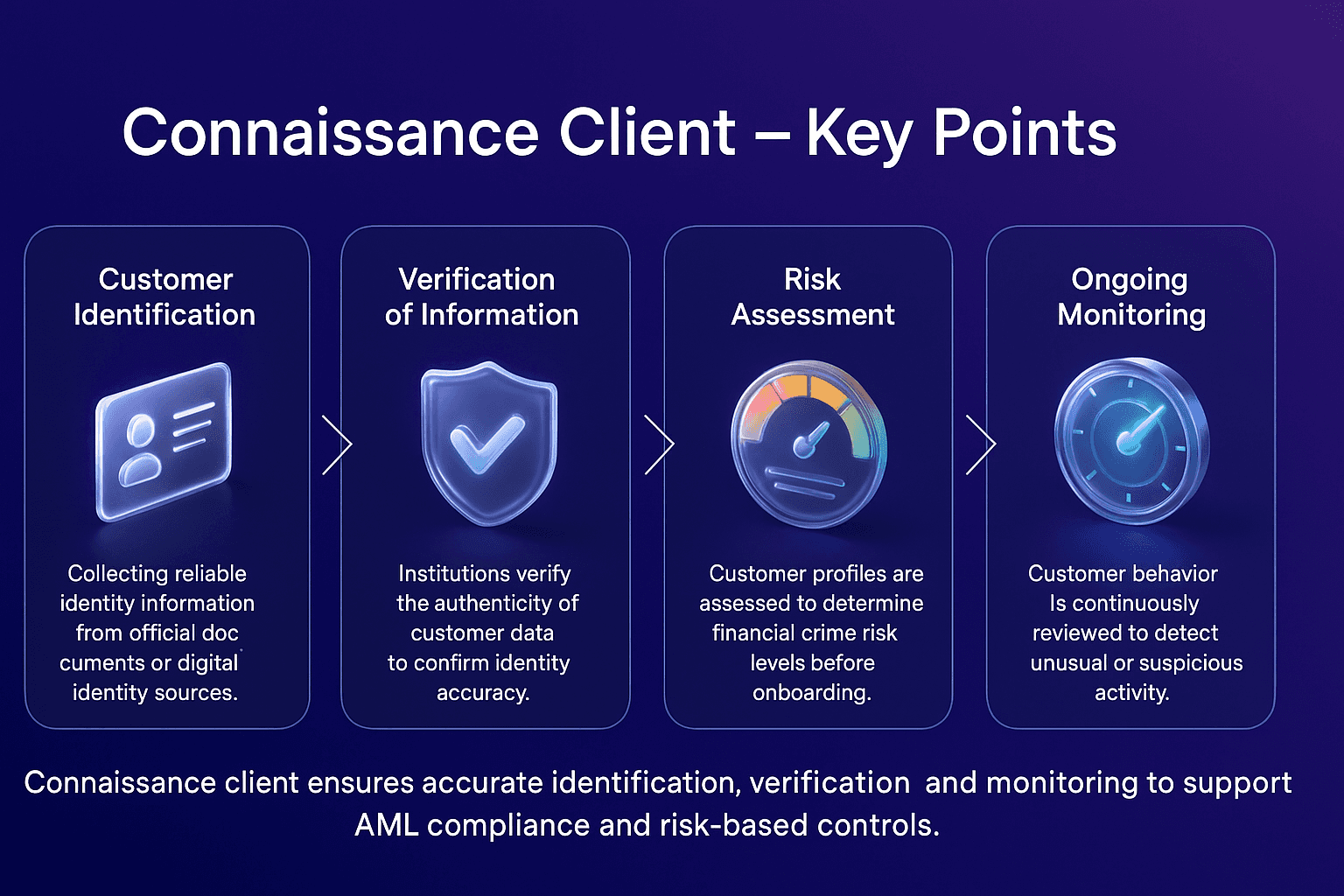
Primary Sanctions
Primary sanctions are restrictions imposed by a government or regulatory authority that prohibit its own citizens, companies, and financial institutions from engaging in specified types of financial activity with sanctioned individuals, entities, or jurisdictions.
For example, U.S. primary sanctions administered by the Office of Foreign Assets Control (OFAC) prohibit U.S. persons and companies from conducting business with individuals or organizations listed on the Specially Designated Nationals (SDN) list.
In AML compliance, understanding and adhering to primary sanctions is essential for preventing violations, avoiding penalties, and maintaining trust with regulators.
Primary Sanctions
Primary sanctions are legal obligations that bind domestic persons and institutions, requiring them to block or restrict transactions with designated entities. Unlike secondary sanctions, which target non-domestic actors, primary sanctions focus on the direct obligations of individuals and businesses under the jurisdiction of the sanctioning authority.
The U.S. Department of the Treasury outlines how primary sanctions prohibit U.S. persons from engaging in transactions with blocked entities, ensuring that sanctioned actors are excluded from the U.S. financial system, as detailed in the OFAC “Basic Information on OFAC and Sanctions” FAQ
Why Primary Sanctions Matter In AML Compliance
Primary sanctions are critical because they directly influence how financial institutions design their compliance frameworks. According to OFAC’s official announcement, firms must have robust systems in place to prevent transactions with sanctioned entities.
Key reasons primary sanctions matter include:
Legal obligation: Breaching primary sanctions can lead to heavy fines and reputational damage
Operational impact: Institutions must screen all customers and transactions against sanctions lists
Risk-based compliance: Sanctions enforcement emphasizes risk awareness across all business lines
Global influence: Even non-sanctioning countries often align with primary sanctions to maintain financial system access
Examples Of Primary Sanctions
Primary sanctions vary by jurisdiction but often include:
U.S. Sanctions: Restrictions by OFAC, such as prohibitions against dealing with entities on the SDN list
EU Sanctions: Measures adopted by the European Union Council restricting EU persons from specific transactions
UK Sanctions: Rules enforced under the UK Sanctions and Anti-Money Laundering Act 2018 requiring UK firms to block dealings with designated persons
Primary Sanctions vs Secondary Sanctions
It’s important to distinguish primary sanctions from secondary sanctions:
Primary sanctions apply to persons and entities under the sanctioning country’s jurisdiction (e.g., U.S. citizens, U.S.-based companies).
Secondary sanctions extend beyond borders, penalizing foreign persons or entities that do business with sanctioned parties.
Together, these measures form a powerful enforcement mechanism in the global AML framework.
The Future Of Primary Sanctions
The future of primary sanctions will be shaped by growing geopolitical complexity and advances in compliance technology.
Trends include:
Broader scope of sanctions to include cyber-related crimes and digital assets
Integration of real-time monitoring tools to ensure instant compliance with sanctions lists
Use of AI and graph analytics to detect hidden networks behind sanctioned entities
Greater alignment of sanctions regimes across the U.S., UK, and EU for coordinated enforcement
Institutions will increasingly need to modernize systems to keep pace with evolving sanctions regimes and regulatory expectations.
Strengthen Your AML Framework With Effective Sanctions Compliance
Adhering to primary sanctions is non-negotiable. By implementing robust screening, monitoring, and adjudication systems, institutions can reduce risk, avoid costly penalties, and ensure regulatory compliance.
👉 Contact Us Today To Strengthen Your AML Compliance Framework
Learn more