Sanctions Screening
A clear, practical guide to the Financial Action Task Force’s 40 Recommendations. Written for compliance teams, auditors, fintech builders, educators, and learners. Ungated and easy to share, this guide can be used as a teaching reference, a policy checklist, and a quick refresher during audits.
Note: This page provides plain-language explanations for educational purposes. For legal obligations, consult applicable laws, regulations, supervisory guidance, and official FATF texts.
Some FATF Recommendations apply primarily to countries and competent authorities. Where relevant, examples below describe how regulated institutions support, align with, or prepare for these requirements rather than implement them directly.
What Is FATF and Why It Matters
The Financial Action Task Force sets global standards for anti-money laundering, counter-terrorist financing, and counter-proliferation financing. Countries adopt these standards through laws and regulations. Examiners assess effectiveness through mutual evaluations. Regulated institutions align policies, controls, data, and technology to the 40 Recommendations within their local legal and supervisory context.
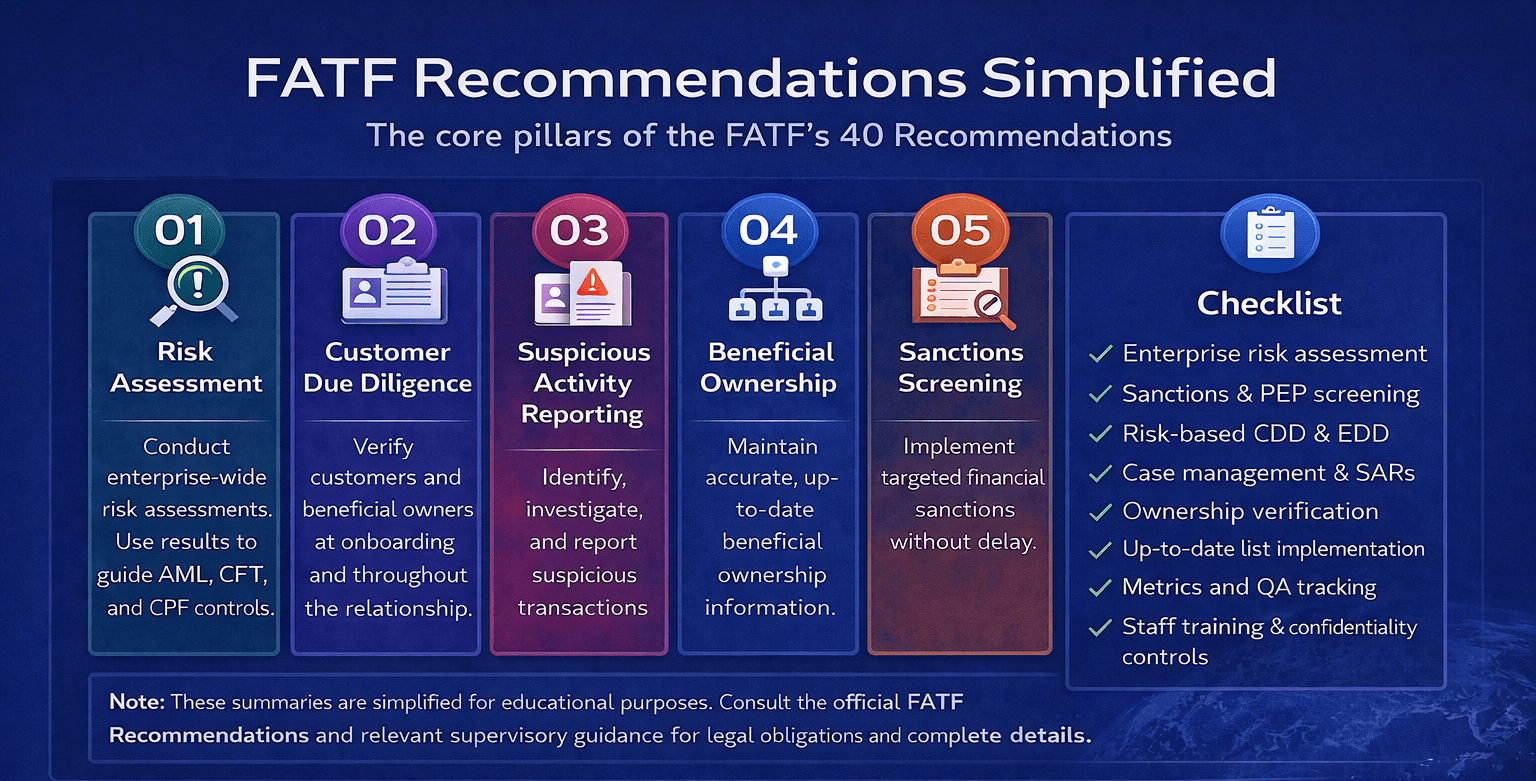
How To Use This Guide
Read the simplified summaries to understand intent. Use the examples to connect controls to daily operations. Map each recommendation to your policies, risk assessment, and control framework. Finish with the checklist to identify gaps and audit readiness issues.
The 40 Recommendations, Simplified With Examples
The recommendations are grouped by theme. Each item includes a plain explanation and a practical, institution-focused example where applicable.
A. Risk, Coordination, and Transparency
This group of recommendations establishes the foundation of a risk-based AML framework. They focus on understanding risk, coordinating across authorities and institutions, and ensuring transparency around ownership and control structures before preventive controls are applied.
R1. Risk-Based Approach
Identify, assess, and mitigate money laundering, terrorist financing, and proliferation financing risks based on your context.
Example: An enterprise-wide risk assessment is approved annually and refreshed when products, geographies, customer profiles, or typologies change.
R2. National Cooperation and Coordination
Countries coordinate AML and sanctions policy across authorities. Institutions align with national risk assessments and supervisory guidance.
Example: Policies reference the national risk assessment and relevant regulator publications.
R3. Money Laundering Offense
Money laundering is criminalised with powers to freeze and confiscate proceeds.
Example: Legal and compliance teams monitor confiscation orders that may impact customer assets or transactions.
R4. Confiscation and Provisional Measures
Authorities must be able to restrain and recover assets.
Example: Case playbooks document how to respond to lawful freezing or restraint requests.
R24. Beneficial Ownership of Legal Persons
Ensure accurate, adequate, and up-to-date beneficial ownership information is available to competent authorities.
Example: Ultimate beneficial ownership is collected and verified during onboarding using documents and reliable registries, with periodic refresh.
R25. Beneficial Ownership of Legal Arrangements
Ensure transparency for trusts and similar arrangements.
Example: Trustee and controlling party information is documented and reviewed regularly.
B. Terrorist Financing and Proliferation Financing
These recommendations address specific risks related to terrorist financing and the proliferation of weapons of mass destruction. Institutions are expected to implement targeted, timely, and proportionate controls that support national and international sanctions regimes.
R5. Terrorist Financing Offense
Criminalise terrorist financing, including attempts and facilitation.
Example: Screening and monitoring scenarios reflect terrorist financing typologies.
R6. Targeted Financial Sanctions Related to Terrorism
Implement targeted sanctions without delay.
Example: Sanctions list updates are implemented as quickly as required, with clear effective timestamps and alerts generated immediately after ingestion.
R7. Targeted Financial Sanctions Related to Proliferation
Implement sanctions related to weapons of mass destruction in line with UN Security Council resolutions.
Example: Watchlists include proliferation financing programs with immediate blocking rules.
R8. Non-Profit Organisations
Apply proportionate, risk-based controls to protect non-profits from terrorist financing abuse.
Example: Due diligence is tailored to the non-profit’s activities, geography, and funding profile.
C. Preventive Measures for Financial Institutions and DNFBPs
Preventive measures translate risk understanding into day-to-day operational controls. This section covers customer due diligence, screening, monitoring, record keeping, and internal governance requirements for financial institutions and designated non-financial businesses and professions.
R9. Secrecy Laws
Customer secrecy laws should not inhibit AML cooperation.
Example: Documented information-sharing procedures exist for lawful disclosures.
R10. Customer Due Diligence
Identify and verify customers and beneficial owners, understand purpose, and conduct ongoing monitoring.
Example: Tiered KYC at onboarding with event-driven and periodic refresh throughout the customer lifecycle.
R11. Record Keeping
Maintain records for the required retention period in your jurisdiction, and ensure they are retrievable.
Example: Centralised storage with audit trails, retention rules, and search functionality.
R12. Politically Exposed Persons
Apply enhanced due diligence to higher-risk PEP relationships.
Example: PEP screening includes relationship mapping and senior management approval for elevated risk cases.
R13. Correspondent Banking
Assess respondent institutions and their AML controls.
Example: Risk questionnaires, sanctions screening, and adverse media checks prior to onboarding.
R14. Money or Value Transfer Services
Ensure MVTS providers are licensed, registered, and monitored.
Example: Policies address agents, sub-agents, and transaction oversight.
R15. New Technologies
Identify and mitigate risks from new products, fintech, virtual assets, and innovative delivery channels.
Example: Model governance covers validation, explainability, change control, and performance monitoring for automated screening systems.
R16. Wire Transfers
Ensure originator and beneficiary information accompanies transfers.
Example: Payment screening validates message fields and rejects transactions with missing data.
R17. Reliance on Third Parties
Manage risks when relying on third parties for CDD.
Example: Contracts include access rights, service levels, and ongoing testing.
R18. Internal Controls and Foreign Operations
Apply group-wide AML programs with consistent standards.
Example: Global policies with local regulatory addendums and training.
R19. Higher-Risk Countries
Apply enhanced measures to higher-risk jurisdictions.
Example: Country risk lists drive enhanced due diligence and transaction controls.
R20. Suspicious Transaction Reporting
Detect and report suspicious activity to the FIU.
Example: Case management supports investigations, SAR preparation, timelines, and audit trails.
R21. Tipping Off and Confidentiality
Protect the confidentiality of suspicious activity reports.
Example: Restricted system access and staff training on disclosure controls.
R22. DNFBPs - Customer Due Diligence
Apply preventive measures to designated non-financial businesses and professions.
Example: Real estate firms implement KYC and suspicious reporting procedures.
R23. DNFBPs - Other Measures
Apply additional controls where relevant.
Example: Casinos perform source of funds checks for higher-risk customers.
D. Transparency Emphasis
This section reinforces the importance of beneficial ownership transparency as a core pillar of the FATF framework. While Recommendations 24 and 25 are addressed earlier, FATF places additional emphasis on accuracy, timeliness, and accessibility of ownership information.
Recommendations 24 and 25 emphasise accuracy, timeliness, and access to beneficial ownership information. Institutions support these objectives through verification, periodic review, and reliable recordkeeping.
E. Authorities and Institutional Readiness
These recommendations focus primarily on the powers and responsibilities of supervisors, financial intelligence units, and law enforcement authorities. For institutions, the emphasis is on preparedness, cooperation, and the ability to respond to lawful supervisory and investigative actions.
R26–R28. Supervision and Regulation
Authorities license, supervise, and enforce compliance.
Example: Institutions maintain inspection readiness materials aligned to supervisory expectations.
R29. Financial Intelligence Units
FIUs analyse and disseminate financial intelligence.
Example: Processes support lawful FIU information requests and disclosures.
R30–R31. Law Enforcement Powers
Authorities investigate and access records with safeguards.
Example: Production orders and requests are routed through legal and compliance.
R32. Cash Couriers
Authorities detect cross-border cash movements.
Example: Where applicable, branches document cash reporting and escalation procedures.
R33. Statistics
Authorities maintain national AML statistics.
Example: Institutions maintain internal metrics that support supervisory and FIU reporting where required.
R34–R35. Guidance and Sanctions
Authorities issue guidance and enforce sanctions.
Example: Regulatory updates are logged, implemented, and reported to senior management.
F. International Cooperation
International cooperation ensures that money laundering, terrorist financing, and proliferation financing risks are addressed across borders. While these obligations sit with states, institutions play a supporting role through lawful information sharing and cross-border readiness.
R36–R40. Cross-Border Cooperation
Countries cooperate through conventions, mutual legal assistance, extradition, and information exchange.
Example: Institutions maintain procedures for responding to lawful cross-border information requests via competent authorities.
Implementation Checklist
The checklist below is designed to help compliance teams assess whether their AML and sanctions framework aligns with FATF expectations in practice. It can be used for internal reviews, audit preparation, and regulatory readiness assessments.
Use this checklist to assess alignment and audit readiness:
Enterprise-wide risk assessment completed and refreshed
Policies mapped to recommendations and local law
Sanctions, PEP, adverse media, and PF screening in place
Risk-based CDD, EDD, and ongoing monitoring documented
Payment screening validates required data fields
Case management supports investigations and SARs
Model governance covers automated systems
Role-specific training and confidentiality controls
Metrics and quality assurance demonstrate effectiveness
Common Pitfalls and Examiner Expectations
During supervisory reviews and audits, examiners frequently focus on how well AML frameworks operate in practice rather than how policies are written.
The points below highlight common weaknesses and recurring themes identified during assessments.
Policies lack operational detail such as thresholds and ownership
Risk assessments are static and not updated for change
Sanctions updates are delayed or poorly documented
Beneficial ownership verification is superficial
SAR timelines are inconsistent or poorly tracked
Using These Standards in Operations
Translating FATF recommendations into daily operations requires mapping regulatory expectations to concrete processes, controls, and supporting technology. If you are documenting a program, this mapping also makes it easier to show auditors how each control supports a specific FATF expectation. The examples below illustrate how different operational capabilities align with specific FATF recommendations.
FATF-aligned operations map controls to recommendations and implement them through process and technology:
Watchlist Management: List ingestion, normalisation, versioning, and governance aligned to R6, R7, R10, R12, R16, and R19
Customer Screening: Continuous screening across onboarding and lifecycle aligned to R10–R12 and R20
Payment Screening: Message validation and sanctions and PF filtering aligned to R16 and R19
Alert Adjudication: Investigation workflows, audit trails, and SAR preparation aligned to R20 and R23
Transaction Monitoring: Behavioural detection, scenario management, and escalation aligned to R10, R11, R20, and R23






